The Group Policy settings for BitLocker startup options are in conflict and cannot be applied
When you receive the error message about Group Policy settings for BitLocker startup options being in conflict, it usually means that there are multiple conflicting configurations applied through Group Policy for BitLocker settings. Here are steps to resolve this issue:
1. Check Group Policy Settings:
You need to review the Group Policy settings applied to BitLocker, particularly around the startup options. This can be done using the Group Policy Management Console (GPMC) or the Local Group Policy Editor.
- Open
gpedit.msc(Local Group Policy Editor) or the Group Policy Management Console. - Navigate to:
Computer Configuration > Administrative Templates > Windows Components > BitLocker Drive Encryption > Operating System Drives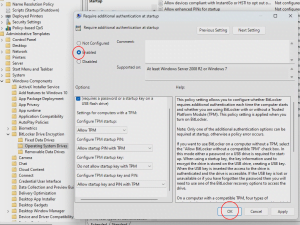
- Review the following settings:
- Require Additional Authentication at Startup
- Configure TPM Startup
- Configure TPM Startup PIN
- Configure TPM Startup Key
- Configure TPM Startup PIN and Key
Ensure that these settings are not contradictory. For example, if one setting requires a startup PIN and another disallows it, there will be a conflict.
2. Resolve Conflicting Settings:
- If you find conflicting settings, adjust them so they align with your desired BitLocker startup configuration.
- You can also try setting the Group Policy setting to “Not Configured” to ensure no conflicting policies are being applied.
3. Update Group Policy:
Once you’ve made the changes:
- Open Command Prompt as Administrator and run the following command to update the Group Policy:
gpupdate /force
4. Check for Inheritance or Multiple Policies:
- If your machine is part of a domain, it’s possible that conflicting policies are being applied from different Group Policy Objects (GPOs). Use the
Resultant Set of Policy (RSoP)orgpresultto check which policies are being applied and identify conflicts.- Run
gpresult /h report.htmlfrom Command Prompt and open the generated report to view the applied GPOs. - Review the policies that are applied at both the local and domain level to spot potential conflicts.
- Run
5. Registry Changes (if needed):
If the conflict persists, you can manually check or modify the registry settings for BitLocker. This can be risky, so make sure you have a backup or consult an IT administrator before proceeding.
- Open
regeditand navigate to:HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE
- Review and adjust any settings that correspond to the conflicting Group Policy settings.
6. Restart the Machine:
After making the necessary changes, restart the machine and try applying BitLocker settings again to verify if the conflict has been resolved.
By resolving these conflicts, you should be able to apply BitLocker policies without issues.
More Resources about bitlocker.
Allow or Deny Write Access to Removable Drives not Protected by BitLocker in Windows
External resources:
Conflict in profiles for Bitlocker encryption using configuration profiles